The Trellix Threat Labs Vulnerability Research team has found an unauthenticated remote code execution vulnerability, filed under CVE-2022-32548 affecting multiple DrayTek routers. The attack can be performed without user interaction if the management interface of the device has been configured to be internet facing. A one-click attack can also be performed from within the LAN in the default device configuration. The attack can lead to a full compromise of the device and may lead to a network breach and unauthorized access to internal resources. All the affected models have a patched firmware available for download on the vendor’s website.
Introduction
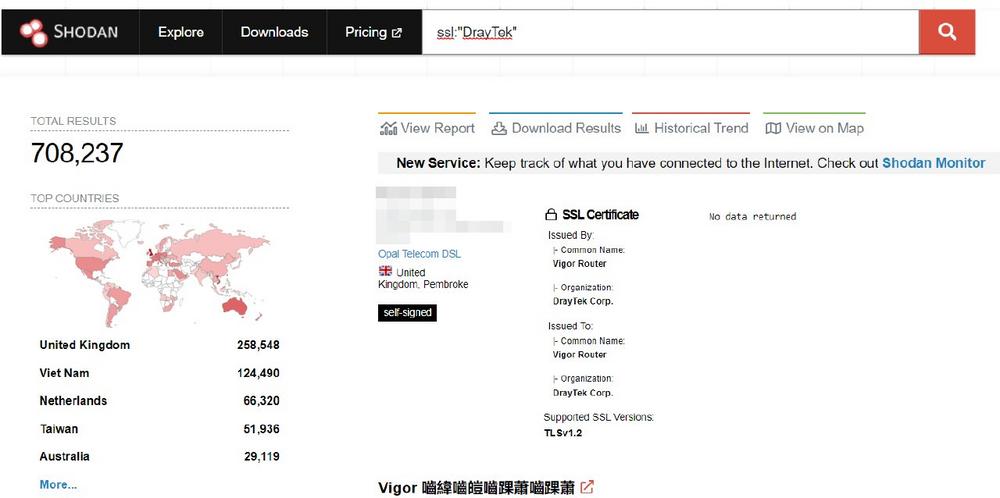
DrayTek is a Taiwanese company that manufactures Small Office and Home Office (SOHO) routers with a wide adoption in the UK, Vietnam, Taiwan, etc. (src: Shodan).
With many businesses implementing work from home policies over the last two years, these affordable devices offer an easy way for Small and Medium Sized Businesses (SMBs) to provide VPN access to their employees. For this reason, we decided to look into the security of one of their flagship products, the Vigor 3910, and found a pre-authentication remote code execution vulnerability affecting the Vigor 3910 and 28 other DrayTek models sharing the same codebase (see Affected Devices below). Exploiting this vulnerability can lead to a complete compromise of the device and can enable a malicious actor to access internal resources of the breached networks.
During our research we uncovered over 200k devices which have the vulnerable service currently exposed on the internet and would require no user interaction to be exploited. Many more devices where the affected service is not exposed externally are still vulnerable to a one-click attack from the LAN. This vulnerability is tracked by MITRE as CVE-2022-32548 with a CVSS 3.0 score of 10.0. A patch has already been released by the manufacturer. If you or your organization are managing DrayTek devices, we recommend that you visit the manufacturer website and apply the patch as soon as possible.
We also applaud DrayTek for their great responsiveness and the release of a patch less than 30 days after we disclosed the vulnerability to their security team. This type of responsiveness and relationship shows true organization maturity and drive to improve security across the entire industry.
Vulnerable devices
The vulnerable devices are as follow:
Vigor3910 < 4.3.1.1
Vigor1000B < 4.3.1.1
Vigor2962 Series < 4.3.1.1
Vigor2927 Series < 4.4.0
Vigor2927 LTE Series < 4.4.0
Vigor2915 Series < 4.3.3.2
Vigor2952 / 2952P < 3.9.7.2
Vigor3220 Series < 3.9.7.2
Vigor2926 Series < 3.9.8.1
Vigor2926 LTE Series < 3.9.8.1
Vigor2862 Series < 3.9.8.1
Vigor2862 LTE Series < 3.9.8.1
Vigor2620 LTE Series < 3.9.8.1
VigorLTE 200n < 3.9.8.1
Vigor2133 Series < 3.9.6.4
Vigor2762 Series < 3.9.6.4
Vigor167 < 5.1.1
Vigor130 < 3.8.5
VigorNIC 132 < 3.8.5
Vigor165 < 4.2.4
Vigor166 < 4.2.4
Vigor2135 Series < 4.4.2
Vigor2765 Series < 4.4.2
Vigor2766 Series < 4.4.2
Vigor2832 < 3.9.6
Vigor2865 Series < 4.4.0
Vigor2865 LTE Series < 4.4.0
Vigor2866 Series < 4.4.0
Vigor2866 LTE Series < 4.4.0
Impact
The compromise of a network appliance such as the Vigor 3910 can lead to the following outcomes (the following is a non-exhaustive list presented in no particular order):
- Leak of the sensitive data stored on the router (keys, administrative passwords, etc.)
- Access to the internal resources located on the LAN that would normally require VPN-access or be present “on the same network”
- Man in the middle of the network traffic
- Spying on DNS requests and other unencrypted traffic directed to the internet from the LAN through the router
- Packet capture of the data going through any port of the router
- Botnet activity (DDoS, hosting malicious data, etc.)
Failed exploitation attempts can lead to:
- Reboot of the device
- Denial of Service of affected devices
- Other possible abnormal behavior
Trellix Threat Labs is not currently aware of any signs of exploitation of this vulnerability in the wild; however, DrayTek devices were recently targeted by various known malicious actors. This was highlighted in the CISA’s memo on the People Republic of China (PRC) compromising SOHO routers and the report from Black Lotus Labs on the ZuoRAT exploiting the Vigor 3900 (end-of-life device replaced by the Vigor 3910). The nature of CVE-2022-32548 makes it harder to exploit compared to past vulnerabilities affecting DrayTek devices, which may hinder threat actors from quickly adopting this vulnerability into their attack frameworks.
Demo video
The following demo video highlights how an attacker could compromise a Draytek router and pivot to internal resources in a mock-network we’ve created.
Technical details
The web management interface of the vulnerable DrayTek devices is affected by a buffer overflow on the login page at /cgi-bin/wlogin.cgi. An attacker may supply carefully crafted username and/or password as base64 encoded strings inside the fields aa and ab of the login page. This would cause the buffer overflow to trigger due to a logic bug in the size verification of these encoded strings. By default, this attack is reachable on the LAN and may be reachable via the internet (WAN) as well if the user has enabled remote web management on their device. The consequence of this attack is a takeover of the so called “DrayOS” that implements the router functionalities. On devices that have an underlying Linux operating system (such as the Vigor 3910) it is then possible to pivot to the underlying operating system and establish a reliable foothold on the device and local network. Devices that are running the DrayOS as a bare-metal operating system will be harder to compromise as it requires that an attacker has better understanding of the DrayOS internals.
We will release more details as of how this bug was found and exploited in our upcoming talk at Hexacon on October 14-15, 2022 and the follow-up blog post that we will publish alongside the presentation.
Detection
Exploitation attempts can be detected by logging/alerting when a malformed base64 string is sent via a POST request to the /cgi-bin/wlogin.cgi end-point on the web management interface router. Base64 encoded strings are expected to be found in the aa and ab fields of the POST request. Malformed base64 strings indicative of an attack would have an abnormally high number of %3D padding. Any number over three should be considered suspicious.
The Trellix Network Security Platform has additionally released rules for exploitation attempts of this vulnerability under the identifier, DrayTek CVE-2022-32548 Buffer Overflow Attempt.
Recommendation
We provide the following recommendations to those potentially affected by a vulnerable DrayTek router:
- Make sure the latest firmware is deployed to your device. You can find the latest firmware by visiting the website of the manufacturer.
- In the management interface of the device, verify that port mirroring, DNS settings, authorized VPN access and any other relevant settings have not been tampered with.
- Do not expose the management interface to the Internet unless absolutely required. If you do, make sure you enable 2FA and IP restriction to minimize the risk of an attack.
- Change the password of affected devices and revoke any secret stored on the router that may have been leaked.
Conclusion
Edge devices, such as the Vigor 3910 router, live on the boundary between internal and external networks. As such they are a prime target for cybercriminals and threat actors alike. Remotely breaching edge devices can lead to a full compromise of the businesses’ internal network. This is why it is critical to ensure these devices remain secure and updated. It’s critical vendors producing edge devices have processes in place for quick and efficient response following vulnerability disclosure, just as DrayTek did. Stay tuned for our next article on DrayTek routers where we will present the process used to uncover this vulnerability.
This document and the information contained herein describes computer security research for educational purposes only and the convenience of Trellix customers. Trellix conducts research in accordance with its Vulnerability Reasonable Disclosure Policy | Trellix. Any attempt to recreate part or all of the activities described is solely at the user’s risk, and neither Trellix nor its affiliates will bear any responsibility or liability.
Trellix
Ohmstr. 1
85716 Unterschleißheim
http://www.trellix.com
![]()